 @Photo by Pixabay
@Photo by Pixabay
“Cyber attacks are one of the top 10 global risks of highest concern in the next decade, with an estimated price tag of 90 trillion dollar if cybersecurity efforts do not keep pace with technological change” - World Economic Forum.[1]
Over the last couple of years the number of successful cyber attacks has surged. To illustrate this: every 39 seconds a cyber attack occurs in the US.[2] Cyber attacks result in the loss of valuable personal data. Email addresses, home addresses, credit card numbers and even complete identities can be stolen. Furthermore, cyber attacks are very harmful to the economy. Estimates of the average cost of a cyber attack range from 369.000 dollar to 3.92 million dollar.[3] In this blogpost, we will dive deeper into the impact of cyber attacks and the importance of cybersecurity.
You have been hacked!
Many people do not even realise it, but there is an extremely high chance that over the course of your life your data has been stolen. Probably even more than once. For example, in November 2019 researcher Vinny Troia found 1.2 billion records exposed, containing among other things 622 million (!!!) unique email addresses.[4] This massive amount of data was leaked in a single data breach and they seem to happen almost every day. Our Twitter feed proves this. Think also of the data breaches of Equifax, Yahoo, Linkedin, Uber and recently Microsoft. All leaking valuable data of hundreds of millions of people. A type of cyber attack that has been increasing in popularity nowadays is a ransomware attack. For example, the potential costs of ransomware attacks over 2019 in the US were 7.5 billion dollar.[5] Institutions, such as municipalities and universities are often the target. At the end of 2019/beginning of 2020 the University of Maastricht in the Netherlands suffered a ransomware attack and allegedly paid a ransom of well over 200.000 euro to gain back control over their system.[6]
Cyber attacks can thus come with huge costs. The annual Hiscox Cyber Readiness report shows some interesting details in this regard. Hiscox investigated more than 5000 enterprises in the US, UK, Spain, Germany, France, Belgium and the Netherlands. According to their research, an average cyber attack in 2019 cost a company 369.000 dollar, up from 229.000 dollar in 2018. Furthermore, 61% of all companies which responded, state that they have experienced a cyber attack over the last year. IBM, together with the Ponemon Institute, made a different calculation and, taking the multiyear costs into account, estimates that on average a data breach costs organisations 3.9 million dollar!!! Over the last 5 years this figure grew with 12%. The Figure below shows the average cost per country according to IBM.[7]
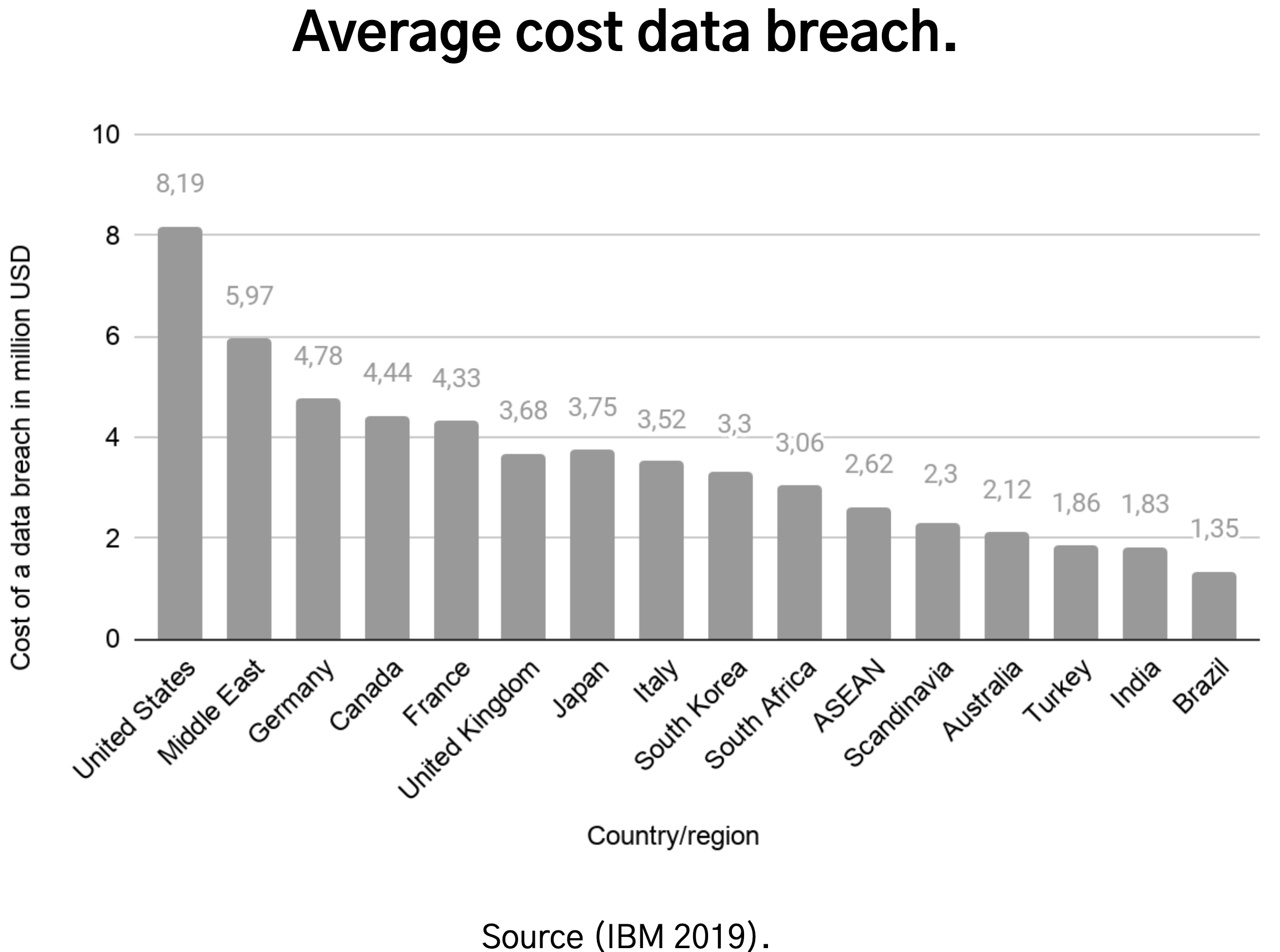
Source (IBM 2019).
Initiatives to improve cybersecurity
If cybersecurity was not already a top priority for individuals and any type of organisation, after reading the above it should be one now. Luckily, there are initiatives and legislation that support endeavors to improve cybersecurity. For example, the EU established a cybersecurity strategy in 2013 and has allocated more than 600 million euro for investments in research and development in cybersecurity projects for the period 2014-2020.[8] Furthermore, in 2004 the European Parliament established ENISA (European Union Agency for Network and Information Security). ENISA “works closely together with Member States and private sector to deliver advice and solutions as well as improving their capabilities” in terms of cybersecurity.[9] A fully private organisation is the European Cyber Security Organisation (ESCO) promotes R&D in cyber security in collaboration with the European Commission and Member States.[10]
A milestone in protecting EU citizens’ data was the implementation of the General Data Protection Regulation (GDPR) in 2018. The main goal of the GDPR is to protect people from others to abuse their data. Fines can amount to up to 4% of the annual revenue of the company committing the crime.[11] To date the most famous convict is Google, who was fined with 50 million euro because i.a. it did not give users enough control over how Google was using their data.[12] The independent European Data Protection Board (EDPB) was established to apply the GDPR and other EU data protection rules in a consistent manner.[13]
Prevention is better than cure
Another essential aspect of data protection is privacy-by-design. The privacy-by-design principle holds that companies make privacy a priority from the initial design stage and throughout the complete further process of software development. Not only will this improve the security of new software, it will also enhance efficiency since prevention is better than cure. A report published by Cisco adds quantitative evidence for this statement. By querying 2800 companies in 13 countries, they found that an initial investment in privacy of 100 dollar results in a total return of 270 dollar in cybersecurity benefits.[14]
Therefore, privacy-by-design is of utmost importance to summitto. Although registering every invoice on a blockchain sounds like storing a lot of data (find out more about our system here), this is not the case. Because we make use of modern cryptography we are able to only register the encrypted fingerprint of the invoice. We do not store any actual data at all. This is a prime example of privacy-by-design. Since the very first design plans of our system, we made privacy and confidentiality our top priority. In this way, our system prevents the loss of valuable invoice data that could hurt the complete economy of a country. Imagine a company, Duck ltd, losing its invoice data to a competitor located in a different country. Duck ltd will suffer significant losses as its competitor now knows exactly which companies to target and against what price it should sell its goods to outcompete Duck ltd.
Also for our other services we always pick the best in class for security. We also employ the general universal second factor to our frontends to make sure account takeovers are of the past.[15] It requires users to login not just with a username and password, but also with a security key. This type of double verification is an internet standard since 2019[16] and is an excellent tool to minimise the risks on successful phishing attacks. But we will talk more about it in another blog post.
To conclude
Summitto believes privacy should be taken very seriously. A lack of cybersecurity affects people on a personal level, hamper the day-to-day business of companies and could harm the complete economy. That’s why we believe in privacy-by-design and that’s why we’re a big supporter of the GDPR. Our own system adheres to these standards and TX++ provides a tool to fight VAT fraud, whilst at the same time it eliminates the risk of costly data breaches. In fact, it does not store any valuable data in the first place. Reach out to us if you want to learn more about our system or if you want to contribute to our project!
-
https://www.cybintsolutions.com/cyber-security-facts-stats/.
-
e.g. https://www.hiscox.co.uk/cyberreadiness# and https://newsroom.ibm.com/2019-07-23-IBM-Study-Shows-Data-Breach-Costs-on-the-Rise-Financial-Impact-Felt-for-Years.
-
https://www.wired.com/story/billion-records-exposed-online/.
-
https://reclaimthenet.org/maastricht-university-pays-ransomware/.
-
https://ec.europa.eu/information_society/newsroom/image/document/2017-3/factsheet_cybersecurity_update_january_2017_41543.pdf
-
https://www.theverge.com/2019/1/21/18191591/google-gdpr-fine-50-million-euros-data-consent-cnil.
-
https://www.securityweek.com/investment-privacy-pays-cybersecurity-dividends-cisco.
- [https://krebsonsecurity.com/2018/07/google-security-keys-neutralized-employee-phishing/](https://krebsonsecurity.com/2018/07/google-security-keys-neutralized-employee-phishing/).
-
w3 (2019). Web Authentication: An API for accessing Public Key Credentials. From: https://www.w3.org/TR/webauthn/.
